Today I came across a bunch of slimy mashup sites that combine images from Google Image Search (your images) with affiliate ads. The attempt is to try to make it look like a legitimate directory or search engine for the topic but what's happening is your images are being used without permission and being attributed to other sites.
CAUTION: Some of the links below may try to inject a worm or trojan.
Go to one of the sites here:
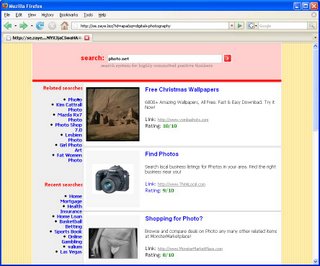
http://www.euc2005.com/photography/Digital-photography.htmlSee those images?
The images are directly from Google Image Search for "Digital Photography":
http://images.google.com/images?hl=en&q=Digital+photography&btnG=Search+Images
Here's the URL to the images from that page:
http://images.google.com/images?q=tbn:RaA8sUkYvwGMCM:Same crap going on from this Polish site too:
http://www.saugus.net/Photos/images/pemigewasset_river.jpg
http://images.google.com/images?q=tbn:WHUZv_rlRPX82M:
http://www.jungleboffin.com/images/artoriginals/digitalpower/6.jpg
http://images.google.com/images?q=tbn:dXhig_gAZri
KQM:http://joecarr.ca/astro/images/2003/2003N707a.jpg
http://images.google.com/images?q=tbn:XoEoJdT29qBX8M:
http://www.kanaphoto.com/img/digital_7.jpg
http://buy-xenical-us.qo.pl/Note that the domain EUC2005.COM is a dummy domain, it's actually pulling up searches in a frame from this site:
http://f-mf.org/search.php?q=digital+photography
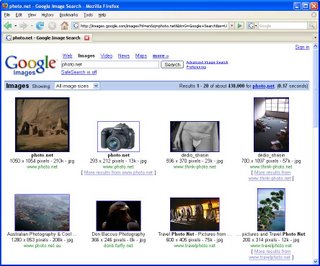
Just for giggles, I did a search for PHOTO.NET in their little search window to see what came up:
Here's the same search in Google Images:
This mess all seems to be hosted on theplanet.com, big shock, on at least 4 servers that I can find, click the IP below for a list of domains:
74.52.114.114I found some of this same crap on every server, click some links from the home pages of these domains and you'll see the same old shit like this:
74.52.114.115
74.52.114.116
74.52.114.117
http://homepage-building.info/carl-bucherer/or this:
http://kdcconstruction.net/morel/or this:
http://internetuniversityincome.com/pantech/etc.
Now let's see who appears to be behind this mess:
Domain ID:D128714698-LRORSomeone else has our copyright infringing buddy listed in an MVPS HOSTS file for some bad things as well:
Domain Name:F-MF.ORG
Created On:11-Sep-2006 11:05:33 UTC
Last Updated On:11-Nov-2006 03:50:00 UTC
Expiration Date:11-Sep-2007 11:05:33 UTC
Sponsoring Registrar:Direct Information PVT Ltd dba PublicDomainRegistry.com (R27-LROR)
Status:OK
Registrant ID:DI_2372832
Registrant Name:Soodkhet Kamchoom
Registrant Organization:N/A
Registrant Street1:2002 E. Tamarack Road
Registrant Street2:
Registrant Street3:
Registrant City:Altus
Registrant State/Province:Oklahoma
Registrant Postal Code:73521
Registrant Country:US
Registrant Phone:+001.5806436662
Registrant Phone Ext.:
Registrant FAX:
Registrant FAX Ext.:
Registrant Email:soodkhet@zlex.org
Name Server:NS1.F-MF.ORG
Name Server:NS2.F-MF.ORG
# [Soodkhet Kamchoom]Now let's see where the base of search operations F-MF.ORG resides:
127.0.0.1 alllinx.info
127.0.0.1 dinet.info #[Trojan.Win32.Small.EV]
127.0.0.1 eqash.net #[eTrust.Win32/Secdrop.JU]
127.0.0.1 frdolls.net
127.0.0.1 frlynx.info
127.0.0.1 joutweb.net
127.0.0.1 linim.net #[eTrust.Win32/Secdrop.JU]
127.0.0.1 linxlive.net
127.0.0.1 lipdolls.net
127.0.0.1 nwframe.net #[Win32/Nitwiz.A]
127.0.0.1 zllin.info #[MHTMLRedir.Exploit][Win32/Dialer.KM]
host F-MF.ORGI looked at the adjacent server IP 66.230.138.194 and BINGO! there's some of the domains listed (in bold) in the MVPS HOSTS files, amazing isn't it?
F-MF.ORG has address 66.230.138.195
whois 66.230.138.195
OrgName: ISPrime, Inc.
OrgID: IPRM
Address: 25 Broadway
Address: 6th Floor, Suite #2
City: New York
StateProv: NY
PostalCode: 10004-1086
Country: US
NetRange: 66.230.128.0 - 66.230.191.255
CIDR: 66.230.128.0/18
alllinx.infoThere's obviously more, but I'm bored chasing this idiot at this time, maybe later.
cleanchain.net
drefus.org
eqash.net
frlynx.info
frsets.info
joutweb.net
linim.net
linxlive.net
nwframe.net
recdir.org
I've been advocating everyone block access from known datacenters and proxy servers for quite some time to stop scraping and other abuse so had the Googlers listened, and I know they heard me, this abuse wouldn't be happening right now and webmasters wouldn't have to deal with this level of abuse.
Sorry to say, I'm going to have to add this line to all my robots.txt for Google, Yahoo and MSN until they resolve this vulnerability:
Disallow: /images/Why won't they listen when I explain what the vulnerabilities are?
Why must we the webmasters have to deal with this garbage?
Firing up the DMCA letters now, several search engines and ISPs are about to be served...
If your images show up on their pages, join me in fighting this good fight.


11 comments:
You don't have to block all images from all robots you can do this.
User-agent: Googlebot-Image
Disallow: /images/
I did it months ago and mine are now finaly out of the image search. I was getting a lot of atempted hotlinking from arab sites.
But I also use
User-agent: *
Disallow: /images/
Google Sitemaps now has settings for its image search.
I'm opting to block all image indexing so I can stop all unauthorized usage beyond just Googlebot because any search engine can be a scrape target until they clean up their act.
OOPS!
I disabled Java ages ago to stop those little cab files from being installed so I never noticed.
I posted a warning.
Here's a shock, that cab file is from inhoster:
host tisall.info
tisall.info has address 85.255.115.227
inetnum: 85.255.112.0 - 85.255.127.255
netname: inhoster
descr: Inhoster hosting company
Screw the DMCA, I informated the host theplanet/ev1 that they have customers with malware installing websites.
Let's see if they take the servers down or not.
74.52.114.112 - 74.52.114.119
PQC Service, LLC
Donetsk
06615
UA
What a small world. Ukraine, just like inhoster.
Hate to tell you this, but .cab files aren't Java. Cab files are a Windows-only archive/install format (often used by MS itself for OS components). Java files are named ending in .jar or .class and browser applets run in a security sandbox and don't install anything. (Vulnerabilities in Java have sometimes been found, but are usually quickly fixed.)
The malware was no sneakier than if it were in a questionable .msi or .exe that was linked to. It does seem that browsers should warn that running .cab and .msi (and some others, like .reg) can change settings on your computer or install stuff. Simply downloading the file ("save as") should be safe for all of those though.
Actually, you're only half right, as the code in the .cab was Java.
Read this link:
http://www.rgagnon.com/javadetails/java-0153.html
They explain how you use CABARC to create a .cab file that can be associated with an applet.
I'm familiar with .jar files too but anyone that's ever played on Pogo games knows they are in Java and download in .cab files.
The malware WAS sneaky on the websites I mentioned that injected it via a bunch of sneaky redirects, you don't know it's happening until it suddenly loads Java and then your virus scanner coughs up an error, if you're lucky.
See, you learned something new :)
Applets delivered by .cab rather than .jar is a new one on me (and stupid, since it would make the site's content only work for Windows users, and probably only IE users as well). Applets still run in a sandbox and shouldn't be able to infect you -- although IE users may find a large gap between "shouldn't" and actual practise.
I haven't heard anything official about any current Firefox Java vulnerabilities however.
I'm not positive the damn thing is actually Java, not like I'm going to dissect the file, but the delivery mechanism seems to be hinged on having Java enabled. Turn it on and going to that page will start download a virus/trojan, turn it off, nothing happens.
What it actually is, I don't know or care, I just know how to avoid it.
Can anyone tell me any way to get drefus.org out of my computer (off of my enternet explorer) Cannot find etc. etc. over and over again ad naseum etc. It's driving me nuts!
Post a Comment